搜索结果: 1-15 共查到“AES”相关记录416条 . 查询时间(0.093 秒)
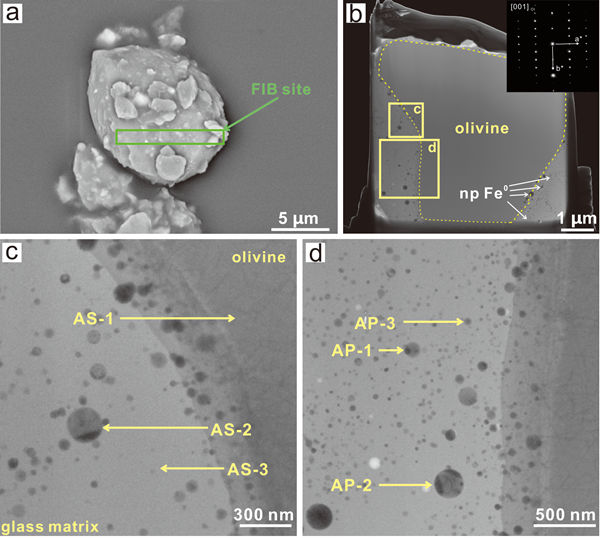
FIB-AES-TEM-EELS联用技术在嫦娥五号月壤样品研究中的应用(图)
FIB-AES-TEM-EELS 联用技术 嫦娥五号 月壤样品研究
font style='font-size:12px;'>
2023/4/4
针对AES最后一轮加密的Cache攻击方法
AES查表法 Rijndael 算法 flush+reload攻击 Cache计时攻击 T表
font style='font-size:12px;'>
2020/8/17
Flush+Reload攻击是以Cache结构构建隐蔽信道,在加密算法执行路径上进行指令攻击,针对OpenSSL0.9.8.b中AES加密代码实现,分析了其加密实现的薄弱点在于一次加密只使用一次Te4表,提出了一种针对AES最后一轮加密实施Flush+Reload攻击的方法;实验结果表明:当收集280×103的AES加密密文和计时数据后,通过表项值与密文值的异或运算,找到最多的共有解可得到最后一...
SPAE a mode of operation for AES on low-cost hardware
secret-key cryptography AES block ciphers
font style='font-size:12px;'>
2019/9/16
We propose SPAE, a single pass, patent free, authenticated encryption with associated data (AEAD) for AES. The algorithm has been developped to address the needs of a growing trend in IoT systems: sto...
A Key-Independent Distinguisher for 6-round AES in an Adaptive Setting
SPN AES Exchange Attack
font style='font-size:12px;'>
2019/8/20
In this paper, we study the results of the recently proposed exchange attack in an adaptive setting. As expected, it leads to present a better 6-round key-independent distinguisher in terms of data an...
桂林理工大学仪器分析课件9-10 AES光源讨论。
Weak-Key Subspace Trails and Applications to AES
AES Key Schedule Weak-Keys
font style='font-size:12px;'>
2019/7/24
Invariant subspaces (Crypto'11) and subspace trails (FSE'17) are two related recent cryptanalytic approaches that led to new results on, e. g. PRINTCipher and AES. We extend the invariant subspace app...
Reducing the Cost of Implementing AES as a Quantum Circuit
quantum cryptanalysis quantum circuit Grover’s algorithm AES
font style='font-size:12px;'>
2019/7/24
To quantify security levels in a post-quantum scenario, it is common to use the quantum resources needed to attack AES as a reference value. Specifically, in NIST’s ongoing post-quantum standardizatio...
AES MixColumn with 94 XOR gates
AES MixColumn Short Linear Program
font style='font-size:12px;'>
2019/7/22
In this short report we present a short linear program for AES MixColumn with 94 XOR gates.
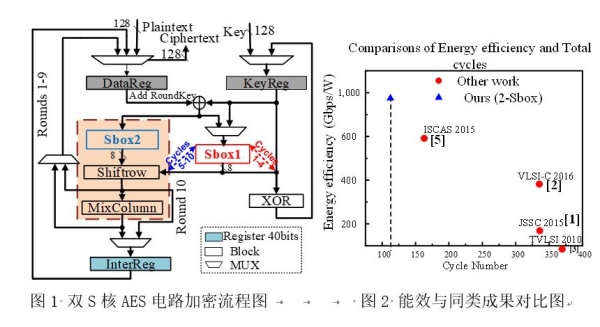
东南大学单伟伟、杨军团队在2019 Symposia VLSI Technology and Circuits国际会议发表高能效AES电路成果(图)
东南大学 单伟伟 杨军 2019 高能效 AES电路
font style='font-size:12px;'>
2019/8/8
2019年6月9至14日,电子科学与工程学院单伟伟教授、杨军教授等赴日本参加Symposia VLSI Technology and Circuits会议。单伟伟教授在Symposium on VLSI Circuits分会的C20 session作报告,主题为“A 923Gbps/W, 113-Cycle, 2-Sbox Energy-efficient AES Accelerator in 2...
New Circuit Minimization Techniques for Smaller and Faster AES SBoxes
AES SBox circuit area circuit depth
font style='font-size:12px;'>
2019/7/15
In this paper we consider various methods and techniques to find the smallest circuit realizing a given linear transformation on nn input signals and mm output signals, with a constraint of a maximum ...
BBQ: Using AES in Picnic Signatures
public-key cryptography AES
font style='font-size:12px;'>
2019/7/10
This works studies the use of the AES block-cipher for Picnic-style signatures, which work in the multiparty-computation-in-the-head model. It applies advancements to arithmetic circuits for the compu...
Dissecting the CHES 2018 AES Challenge
AES CTF
font style='font-size:12px;'>
2019/7/10
One challenge of the CHES 2018 side channel contest was to break a masked AES implementation. It was impressively won by Gohr et al. by applying ridge regression to obtain guesses for the hamming weig...
Practical Attacks on Reduced-Round AES
AES Zero-difference Secret-key distinguisher
font style='font-size:12px;'>
2019/7/8
In this paper we investigate the security of 5-round AES against two different attacks in an adaptive setting. We present a practical key-recovery attack on 5-round AES with a secret s-box that requir...
Mixture Integral Attacks on Reduced-Round AES with a Known/Secret S-Box
AES Mixture Differential Cryptanalysis Secret-Key Distinguisher
font style='font-size:12px;'>
2019/7/8
The starting point of our work is “Mixture Differential Cryptanalysis” recently introduced at FSE/ToSC 2019, a way to turn the “multiple-of-8” 5-round AES secret-key distinguisher presented at Eurocry...
Scrutinizing the Tower Field Implementation of the $\mathbb{F}_{2^8}$ Inverter -- with Applications to AES, Camellia, and SM4
Tower field Inverter S-box
font style='font-size:12px;'>
2019/6/24
The tower field implementation of the F28F28 inverter is not only the key technique for compact implementations of the S-boxes of several internationally standardized block ciphers such as AES, Camell...


