搜索结果: 1-15 共查到“interactive”相关记录382条 . 查询时间(0.078 秒)
RAF22, ABI1 and OST1 form a dynamic interactive network that optimizes plant growth and responses to drought stress in Arabidopsis
ABA signaling RAF22 ABI1 OST1 phosphorylation
font style='font-size:12px;'>
2023/11/28
Plants adapt to their ever-changing environment via both positive and negative signals induced by environmental stimuli. Drought stress, for instance, induces the accumulation of the plant hormone abs...
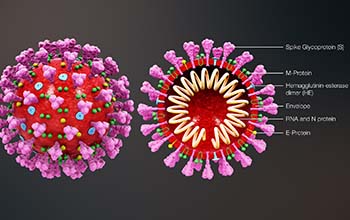
Interactive model explores how different interventions affect COVID-19 spread(图)
Interactive model explores interventions COVID-19 spread
font style='font-size:12px;'>
2020/4/10
Millions of Americans confined to their homes to help curb the spread of the novel coronavirus, COVID-19, have a pressing question on their minds: How long does social distancing need to last?To explo...
Randomly Rotate Qubits Compute and Reverse --- IT-Secure Non-Interactive Fully-Compact Homomorphic Quantum Computations over Classical Data Using Random Bases
Homomorphic encryption Quantum cryptography Information-theoretic security
font style='font-size:12px;'>
2019/9/16
Homomorphic encryption (HE) schemes enable processing of encrypted data and may be used by a user to outsource storage and computations to an untrusted server. A plethora of HE schemes has been sugges...
Non-Interactive Zero Knowledge Proofs in the Random Oracle Model
FS transform NIZK random oracle model
font style='font-size:12px;'>
2019/8/22
The Fiat-Shamir (FS) transform is a well known and widely used technique to convert any constant-round public-coin honest-verifier zero-knowledge (HVZK) proof or argument system CIPC=(Prov,Ver)CIPC=(P...
Decentralized Multi-authority Anonymous Authentication for Global Identities with Non-interactive Proofs
anonymous authentication attribute collusion attack
font style='font-size:12px;'>
2019/6/14
We propose a decentralized multi-authority anonymous authentication scheme in which a prover and a verifier are non-interactive. We give two security definitions; resistance against collusion attacks ...
Black-Box Language Extension of Non-Interactive Zero-Knowledge Arguments
NIZK USS-NIZK black-box construction
font style='font-size:12px;'>
2019/6/13
Highly efficient non-interactive zero-knowledge arguments (NIZK) are often constructed for limited languages and it is not known how to extend them to cover wider classes of languages in general. In t...
Simultaneous Amplification: The Case of Non-Interactive Zero-Knowledge
NIZK Security Amplification
font style='font-size:12px;'>
2019/6/4
We develop novel techniques to leverage the use of leakage simulation lemma (Jetchev-Peitzrak TCC 2014) to argue amplification. A crucial component of our result is a new notion for secret sharing NPN...
DLSAG: Non-Interactive Refund Transactions For Interoperable Payment Channels in Monero
Linkable Ring Signature Payment Channel Blockchain
font style='font-size:12px;'>
2019/6/3
Monero has emerged as one of the leading cryptocurrencies with privacy by design. However, this comes at the price of reduced expressiveness and interoperability as well as severe scalability issues. ...
Non-Interactive MPC with Trusted Hardware Secure Against Residual Function Attacks
Non-Interactive MPC Communication round complexity Trusted hardware
font style='font-size:12px;'>
2019/5/9
Secure multiparty computation (MPC) has been repeatedly optimized, and protocols with two communication rounds and strong security guarantees have been achieved. While progress has been made construct...
A Tight Parallel-Repetition Theorem for Random-Terminating Interactive Arguments
parallel repetition interactive argument smooth KL-divergence
font style='font-size:12px;'>
2019/4/22
Soundness amplification is a central problem in the study of interactive protocols. While ``natural'' parallel repetition transformation is known to reduce the soundness error of some special cases of...
Theory and application of computationally independent one-way functions: Interactive proof of ability - Revisited
one-way functions zero knowledge proof computational independence
font style='font-size:12px;'>
2019/4/1
We introduce the concept of computationally independent pair of one-way functions (CI-OWF). We also provide two rich classes of examples of such functions based on standard assumptions. We revisit two...
A Note on Key Agreement and Non-Interactive Commitments
Non-interactive commitments key agreement
font style='font-size:12px;'>
2019/3/13
We observe that any key agreement protocol satisfying perfect completeness, regardless of its round complexity, can be used to construct a non-interactive commitment scheme.
VIRTUALISING AN OTTOMAN FORTRESS – LASER SCANNING AND 3D MODELLING FOR THE DEVELOPMENT OF AN INTERACTIVE, IMMERSIVE VIRTUAL REALITY APPLICATION
3D HTC Vive modelling reconstruction virtual reality
font style='font-size:12px;'>
2019/3/4
“A picture is worth a thousand words”: a famous quote about knowledge dissemination but also literally true. The documentation of cultural heritage (CH) monuments is carried out by measurements and ph...
INTERACTIVE IMAGE GEOLOCALIZATION IN AN IMMERSIVE WEB APPLICATION
3D web application historical images pose estimation
font style='font-size:12px;'>
2019/3/2
For a long time people have been interested in the past and history and how we can go back in time using a time machine. And while we cannot invent a time machine, at least not yet, we can create a vi...
RECREATE THE ANCIENT URBAN LANDSCAPE. MULTIMEDIA AND INTERACTIVE TOOLS TO IMPROVE ACCESSIBILITY AND ENHANCEMENT OF THE ARCHAEOLOGICAL HERITAGE OF MILAN
Milan archaeology accessibility enhancement three-dimensional documentation
font style='font-size:12px;'>
2019/3/2
The urban archaeological remains, especially in cities like Milan, have a number of issues closely related to the preservation and maintenance of the characteristics of each site, but today these issu...

